Extended IPv4 ACL Drill 1 – Answers
The previous post listed a set of ACL requirements that require an IPv4 Extended ACL. Your job: using those requirements, configure an extended named ACL. Of course, this post makes no sense without the post that states the requirements, so check out that post first. Answers and comments are below the fold.
Ground Rules
Often times, the words that describe the requirements for an ACL can be interpreted in several ways. So, before reading these answers, consider:
- Your answer may be correct per your interpretation of the requirements…
- …while being different from the answer listed here.
For the answer shown here, I tried to work through the requirements one by one, with a line in the ACL for each requirement. Feel free to comment about alternate answers, but FYI, that’s how I came up with these.
On to the answers!
Subnets in Use
All the answers will use the subnets of host A and Server S, so a few words about those first.
To match the subnet of host A, you need to find the subnet ID and the matching wildcard mask. First, calculate the subnet ID:
- R1’s G0/1 interface address/mask is 172.16.1.1/25
- Calculate the subnet ID as 172.16.1.0.
Then, to find the correct wildcard (not subnet) mask to use:
- Convert prefix mask /25 to dotted decimal mask 255.255.255.128
- Subtract it from 255.255.255.255 to get 0.0.0.127
- Use 0.0.0.127 as the wildcard mask in the ACL statement.
For subnet 3, using the same logic:
- R3’s G0/1 interface address/mask is 172.16.3.3/27
- To match the subnet, use the subnet ID of 172.16.3.0.
- Convert prefix mask /27 to dotted decimal mask 255.255.255.224
- Subtract it from 255.255.255.255 to get 0.0.0.31
- Use 0.0.0.31 as the wildcard mask.
Answers
Of note for this particular answer:
- The ACL is located on R2, in the direction pointing towards the server, so any matching of well-known ports should be a match of the ACL’s destination port number
- Any ACL statement that matches a port number should use either the tcp or udp keywords.
- As an outbound ACL, the ACL will no filter any messages created by the router itself. So, the ACL would not consider filtering any ARP or OSPF messages it had generated anyway. (More on this topic in the answers for Option 3.)
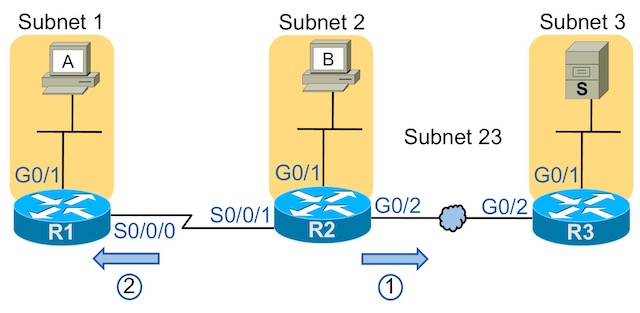
Figure 1: Topology Used in the ACL Drill
The answers for requirement set 1, for the explicitly identified applications:
ip access-list extended option1 permit tcp 172.16.1.0 0.0.0.127 172.16.3.0 0.0.0.31 eq 23 # uses 23 for Telnet permit tcp 172.16.1.0 0.0.0.127 172.16.3.0 0.0.0.31 eq 80 # uses 80 for WWW permit tcp 172.16.1.0 0.0.0.127 172.16.3.0 0.0.0.31 eq 25 # uses 25 for SMTP
Partial Answer
The requirement about denying all other TCP and UDP packets, while permitting all other IP packets besides those, might be a bit tricky. The logic intended by the combined requirements is this sequence:
- Permit packets for apps Telnet, World Wide Web, and SMTP
- Deny all other TCP and UDP traffic (that wasn’t already permitted)
- Permit all other IP traffic (that wasn’t already denied)
With that in mind, the following answer adds the matching for all other TCP, then UDP, and then IP. Without those final three commands, all other IP packets would have been denied because of the implied deny any any at the end of the ACL. (Also note that the configuration enables the ACL as suggested in the lab.)
ip access-list extended option1 permit tcp 172.16.1.0 0.0.0.127 172.16.3.0 0.0.0.31 eq 23 # uses 23 for Telnet permit tcp 172.16.1.0 0.0.0.127 172.16.3.0 0.0.0.31 eq 80 # uses 80 for WWW permit tcp 172.16.1.0 0.0.0.127 172.16.3.0 0.0.0.31 eq 25 # uses 25 for SMTP deny tcp any any deny udp any any permit ip any any ! interface gigabitethernet0/2 ip access-group option1 out
Completed Answer

Hi Wendell and thanks a lot for your knowledge provided through your blog.
My question is the following:
It is clear that as an outbound ACL, the ACL will no filter any overhead packets created by the R2 router itself. But what happened with the overhead packets created by the R1 and pass through the R2 G0/2 interface?
Is it possible for example the RIPv2 protocol to work correctly for the whole network implementation when a “deny udp any any” statement listed in the ACL?
Please let me also know if the last entry “permit ip any any” is used to avoid filtering of the OSPF packages created by the R1?
Thanks in advance.
Ioannis
Ioannis,
Thanks for the note! You’re welcome.
On your question 1: Overhead created by R1, that is then forwarded by R2, would be considered by an outbound ACL on R2. However, what overhead protocol on R1 generates messages that R2 would forward? EG, R1 sends RIP messages to R2. R2 processes those RIP messages, and then discards them. The RIP messages R2 sends are generated by R2. Same idea for other routing protocols (except BGP), same idea with CDP, routers don’t forward ARP…
On your #2: a deny udp any any on an ACL applied in the outbound direction, on every router interface, should indeed allow RIP to work throughout the network, for the reasons stated above.
On your #3, because this ACL is applied outbound, it wouldn’t matter to OSPF messages generated by the router. But if using it as an inbound, indeed, because OSPF does not use TCP nor UDP, inbound OSPF message would match the permit ip any any at the end of the list.
Hope this helps
Wendell
Diagram has two routers labeled R2
Hi Wendell, I’m not sure about stage 3 for subnet 3, why convert prefix mask /25 to dotted decimal mask 255.255.255.224? I would have used a /27 from router 3 G0/1. Why a /25?
Hi Chris,
There was a typo. It’s now fixed. thanks, wendell