Free Play Labs – CCNA Vol 2, Chapter 6
Switch port security filters incoming frames based on the source MAC address. Simple enough, right? Well, this long-time switch security feature has more than a few twists. Chapter 6 of the CCNA 200-301 Cert Guide Volume 2 covers Port Security – use this post to get a little help to recreate the book’s examples from that chapter. Good learning!
Confused? New to “Free Play” Labs?
The idea is simple: Many students would like to further explore the Examples in the Official Cert Guide. We remove the barriers so you can do just that with the free Cisco Packet Tracer simulator.
The details require some reading. To get your head around what kind of content is here in the blog for these labs, read:
Book: CCNA 200-301 OCG, Volume 2
Chapter: 6
Title: Implementing Switch Port Security
Part: 2
What’s in This Post
Chapter Intro: A brief description of the topics in that chapter of the book.
Download Link: Links to a ZIP; the ZIP holds all the .PKT files for this chapter.
Table of PKT files, by Example: A table that lists each example in the chapter, with the files supplied for each. Also lists a note about whether the PKT topology matches the book example exactly or not.
Tips: When we build the files, we come across items that we think might confuse you when trying the examples with PT. We write those notes in this section!
Chapter Intro
Chapter 6 of the CCNA 200-301 Official Cert Guide, Volume 2 discusses Cisco switch port security, from concepts, configuration, to verification. Once enabled on an interface, port security adds logic for each incoming frame, comparing the source MAC address of the frame versus a table and a few other logic steps. The result can be to allow the frame to continue as normal, but the other results can be a variety of steps to prevent the traffic, from simply discarding that frame to both discarding the frame and disabling the interface.
Port security allows us to configure several settings to match incoming frames, including:
- A list of allowed source MAC addresses – both statically defined and dynamically learned
- A number of different source MAC addresses
- An option to store dynamically-learned MAC addresses in the configuration
- Options for three sets of actions to take, called modes: shutdown, violate, and restrict
Packet Tracer has solid support for the port security feature, so join in, configure the features, and experiment with the verification commands.
One .PKT File – But Maybe Two (Duplicate) Toplogies
When building the content for this post, we review the examples in the book and decide whether it makes sense to supply a Packet Tracer (.pkt) file to match the example. If we choose to support an example by supplying a matching .pkt file, the .pkt file includes a topology that matches the example as much as possible. It also includes the device configurations as they should exist at the beginning of the example.
In some cases, the .pkt file shows two instances of the lab topology – one above and one below. We include two such topologies when the book example includes configuration commands, for these purposes:
- Top/Initial: The topology at the top has the configuration state at the beginning of the example.
- Bottom/Ending: The topology at the bottom adds the configuration per the example, so that it mimics the configuration at the end of the example.
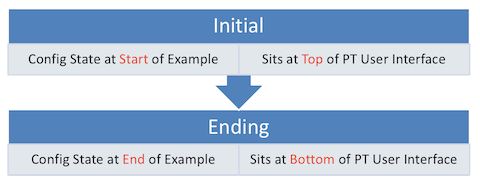
Table of .PKT Files, by Example
|
Example |
.PKT Includes Initial State of Example? | .PKT Also Includes Ending State of Example? | Exact Match of Interface IDs? |
| 6-1 | Yes | Yes | Yes |
| 6-2 | Yes | No | Yes |
| 6-3 | Yes | No | Yes |
| 6-4 | Use 6-3 | No | Yes |
| 6-5 | Yes | No | Yes |
| 6-6 | Use 6-5 | No | N/A |
| 6-7 | Yes | No | N/A |
| 6-8 | Yes | No | N/A |
Tips
Note that the initial state in this .pkt does not include the Port Security configuration shown in the example, with the ending state of the .pkt including the configuration in the example.
Also, the book does not detail the IP addresses of the hosts in the related figure, but the .pkt file includes pre-configured IP addresses as follows, for easier testing:
- Server1 10.1.1.1 /24
- Server2 10.1.1.2 /24
- PC3 10.1.1.3 /24
- PC4 10.1.1.4 /24
- PC5 10.1.1.5 /24
- PC6 10.1.1.6 /24
Note: This example is based on the configuration added in Example 6-1.
Also, note that in Packet Tracer, the show running-config interface f0/2 does not work. The command would work on real gear. Use instead the show running-config command.
Note: This example is based on the configuration added in Example 6-1.
The output shown in the example matches a particular scenario when testing. To re-create that scenario, so that the output best matches the book’s output:
- Open the command prompt on the “Company Comptroller” PC and ping 10.1.1.1 (Server 1) and 10.1.1.2 (Server 2).
- Server 1, whose MAC has been defined as 0013.197b.5004 in this lab, will reply and cause a Port Security violation to match the output.
- Server 2, whose MAC has been defined as 0200.2222.2222, will reply, not cause a violation, but the output will list server 2’s MAC in the output.
PT does not support several of the commands shown in the example. However, you can use these commands to find most of the same output, although you will have to ignore unrelated output:
- show mac address-table interface F0/2
- show mac address-table dynamic
Note that Example 6-5 and onward in this chapter do not continue the same scenario as shown in Examples 6-1, 6-2, 6-3, and 6-4.
IP reference:
- PC1 10.1.1.1 /24
- PC3 10.1.1.3 /24
To re-create the output in the example:
- Open a command prompt on PC1 and ping 10.1.1.3 (PC3).
- PC3 will send a reply, causing a violation.
Although this example is based on the same .pkt file as Example 6-5, re-open the .pkt file to begin your experiments with Example 6-6 to reset the beginning state.
IP address reference:
- PC1 10.1.1.1
- PC3 10.1.1.3
Suggestion: Make the switch SW1 CLI visible for the entire experiment so you can see when the switch disables the port.
To re-create the output in the example:
- Open a command prompt on PC1 and ping 10.1.1.3 (PC3).
- PC3 will send a reply, causing a violation.
The show interface f0/13 status command does not work in PKT. Use the show interface f0/13 command instead.
To re-create the output in the example:
- Open a command prompt on PC1 and ping 10.1.1.3 (PC3).
- PC3 will send a reply, causing a violation.
To re-create the output in the example:
- Open a command prompt on PC1 and ping 10.1.1.3 (PC3) repeatedly.
- PC3 will send a reply, causing a violation.
- Issue commands on switch SW1, seeing the violation count increase
Repeat the above steps to confirm the counter keeps increasing.
Note: PT does not issue log messages in reaction to port security events, while real Cisco switches issue the messages as those shown in the example.

What are the passwords to enable mode passwords on the devices in your packet tracer labs?
Here is the link to the overview of the Labs
https://www.certskills.com/packet-tracer-labs/
All passwords are “cisco”