Free Play Labs – CCNA Vol 2, Chapter5
As with all the blog posts in this series, this post helps you with working through how to perform the examples in the CCNA 200-301 Cert Guides (Volumes 1 and 2) using Cisco’s Packet Tracer tool. However, this next chapter is a little strange in that it includes only a small amount of configuration. But it’s worth doing the short number of examples – so keep reading!
Confused? New to “Free Play” Labs?
The idea is simple: Many students would like to further explore the Examples in the Official Cert Guide. We remove the barriers so you can do just that with the free Cisco Packet Tracer simulator.
The details require some reading. To get your head around what kind of content is here in the blog for these labs, read:
Book: CCNA 200-301 OCG, Volume 2
Chapter: 5
Title: Securing Network Devices
Part: 2
What’s in This Post
Chapter Intro: A brief description of the topics in that chapter of the book.
Download Link: Links to a ZIP; the ZIP holds all the .PKT files for this chapter.
Table of PKT files, by Example: A table that lists each example in the chapter, with the files supplied for each. Also lists a note about whether the PKT topology matches the book example exactly or not.
Tips: When we build the files, we come across items that we think might confuse you when trying the examples with PT. We write those notes in this section!
Chapter Intro
This chapter has a short list of short examples, all about securing the CLI of a router or switch. The subjects: passwords and ACLs applied to the login process. No need for a lot of reading here – just dive in and repeat the examples!
One .PKT File – But Maybe Two (Duplicate) Toplogies
When building the content for this post, we review the examples in the book and decide whether it makes sense to supply a Packet Tracer (.pkt) file to match the example. If we choose to support an example by supplying a matching .pkt file, the .pkt file includes a topology that matches the example as much as possible. It also includes the device configurations as they should exist at the beginning of the example.
In some cases, the .pkt file shows two instances of the lab topology – one above and one below. We include two such topologies when the book example includes configuration commands, for these purposes:
- Top/Initial: The topology at the top has the configuration state at the beginning of the example.
- Bottom/Ending: The topology at the bottom adds the configuration per the example, so that it mimics the configuration at the end of the example.
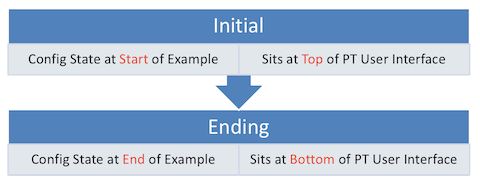
Table of .PKT Files, by Example
|
Example |
.PKT Includes Initial State of Example? | .PKT Also Includes Ending State of Example? | Exact Match of Interface IDs? |
| 5-1 | Yes | Yes | N/A |
| 5-2 | Yes | Yes | N/A |
| 5-3 | Not supported | No | N/A |
| 5-4 | Yes | Yes | N/A |
Tips
Note: In the book, the caption for Example 5-2 suggests an enable secret password of “cisco”, but the example instead shows a password of “fred”. The errata is due to be updated to list “fred” in the caption; the PT file uses “fred” as well.
Cisco Packet Tracer does not support the algorithm-type keyword on the enable configuration command, which is the main point of this example, so we did not supply a .pkt file.
The example show configuration only, so the .pkt file shows an initial state (without the configuration) and ending state (with the configuration added.)
Also, note that the book does not show the context of the example, but to better learn the points when recreating the example, we added a topology to go with the single router. In this case, PC1 on the left is in the subnet that the ACL allows to Telnet to the router, while PC2 on the right is in a subnet that should be denied per the ACL. You can test with the command-line telnet command in the PCs.

Is it possible to sort or list the blog posts by volume and chapter, instead of by date?
Sure! Look up at the top of the page at the menus. To two left-most menu items are for Vol 1 and Vol 2. Once expanded, you can click on any book “Part”, and see all this site’s posts that relate to a part. Or, hover over a book part, and the menu will expand to the individual chapters – so you can also select blog posts related to a chapter.
Hey Wendell. Where is the lab exercise?
Hi Ermundo,
Check out this link, from up in the “New to Cert Guide Packet Tracer Labs” section: https://www.certskills.com/packet-tracer-labs/
Short version: Of the two types of labs here at my blog, this type is a free-play style lab. I help you re-create the same scenario used to create examples in my books, and then you can explore from there. No lab steps.
The other style, which I call “Config Labs”, are short configuration-focused lab exercises with requirements for you to follow. Check out: https://www.certskills.com/config-labs/ for more info.
For both, use the heading menu of “Hands On”, with two subitems, which are the two types of labs.
Wendell